SITE-TO-SITE VPN WITH ROUTING TO ACCESS SOFTLAYER NETWORK
Step-by-step guide
- Order Vyatta Gateway Appliance
- Order IPSEC VPN
- Span your private VLAN to the private VLAN of the Vyatta Gateway Appliance in VLANs page
- Associate your VLAN with the private VLAN of the Vyatta Gateway Appliance in Gateway Appliances > Firewall Details Page
-
Create IPSEC VPN at Softlayer End
- Create IPSEC VPN on the Sophos UTM and confirm status is up
-
Add a virtual Interface on the Vyatta Gateway Appliance console (or webpage)
- Create a source NAT rule to allow any traffic from your private VLAN NAT through your public interface of the Vyatta to allow internet traffic out from you
- Create a firewall rule to allow traffic out to anywhere from your private (server) VLAN
- Route your private VLAN with the private VLAN of the Vyatta Gateway Appliance in Gateway Appliances > Firewall Details Page
- Done!
1. Order Vyatta Gateway Appliance and
2. Order IPSEC VPN
This took a lot more time than it should have done to order the appliance but the IPSEC VPN was immediate.
3. Span your private VLAN to the private VLAN of the Vyatta Gateway Appliance in VLANs Page
Login to the Softlayer console and Select Network from the drop down Menu > IP Management > VLANs
Press the Span tab > Select VLAN Spanning to On.
4. Associate your VLAN with the private VLAN of the Vyatta Gateway Appliance in Gateway Appliances > Firewall Details Page
Login to the Softlayer console and Select Network from the drop down Menu > Gateway Appliances > Then click on the firewall.
Under the Associate a VLAN > select our private VLAN from the drop down (fakevlanid101) and click Associate and then > update Device.
5. Create IPSEC VPN at Softlayer End
Login to the Softlayer console and Select Network from the drop down Menu > IPSEC VPN
Remote Peer Address is 1.1.1.1, Pre-shared Key can be anything as long as you put in the same details on the Sophos UTM.
I went the defaults – i.e. 3DES / MD5 with DH Group 2 for both phases and key life 7800 for Phase one and 3600 for Phase two. PFS enabled.
Customer Subnets should be 192.168.0.0/24.
Hosted subnet should be 10.10.10.0/24 and 10.11.11.0/24 to allow access to both the Vyatta private VLAN and the server private VLAN
6. Create IPSEC VPN on the Sophos UTM and confirm status is up
Login to the Sophos UTM > Site-to-Site VPN > IPsec > Policies > Find TripleDES PFS and then Clone. I renamed it Softlayer TripleDES PFS. Copy the details from step 5 and save.
Login to the Sophos UTM > Site-to-Site VPN > IPsec > Remote Gateway > + New Remote Gateway > Name Softlayer, Initiate Connection > Add the Gateway using the Public IP Address of the Vyatta Gateway Appliance (found on the Softlayer console by Selecting Network from the drop down Menu > Gateway Appliances > Then click on the firewall.) in this case 2.2.2.2.
Authentication type should be “Preshared Key” and then use the key created at step 5. Add the remote networks which in this case are 10.11.11.0/24 (server private VLAN) and 10.10.10.0/24 (Vyatta private VLAN)
Login to the Sophos UTM > Site-to-Site VPN > IPsec > Connections > + New IPsec Connection > Name – Softlayer VPN > Remote Gateway- Softlayer (just created), Local Interface – External (WAN), Policy – Softlayer TripleDES PFS (just created). Local Networks – Internal.
Login to the Sophos UTM > Site-to-Site VPN – check the status which should now be green – see image (note IP addresses have been production blacked out):
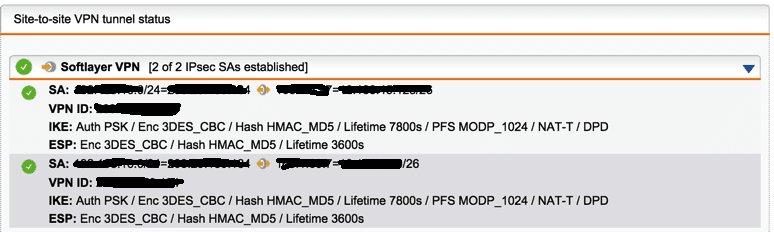
7. Add a virtual Interface on the Vyatta Gateway Appliance console (or webpage)
Login to the Vyatta firewall by SSH, the details will be in the Firewall details page above – in this case 10.10.10.10, Vyatta as the username and password in the Firewall details page.
config
set interfaces bonding bond0 vif 101 address 10.11.11.0/24
commit
save
8. Create a source NAT rule to allow any traffic from your private VLAN to go out through your public interface of the Vyatta to allow internet traffic out from you
Login to the Vyatta firewall by SSH, the details will be in the Firewall details page above – in this case 10.10.10.10, Vyatta as the username and password in the Firewall details page.
config
set nat source rule 10 source address ‘10.11.11.0/24′
set nat source rule 10 outbound-interface ‘bond1’
set nat source rule 10 translation address ‘masquerade’
commit
save
9. Create a firewall rule to allow traffic out to anywhere from your private (server) VLAN
I had to do this using the Web GUI as I am new to Vyatta. Log in with https://10.10.10.10 > Select the Configuration Tab > then on the left, Firewall > Network Group > Create new Network Group called HMQ-Subnet > for the Network value double click then 10.11.11.0/24 > then press the commit button.
Then go to Firewall > Name > create – call it 101. Default action = accept. A rule line appears on the left. Create Rule – 1. Action – accept. Protocol – All > Set.
Under rule 1 on the left, select Destination > 0.0.0.0/0 as the address, leave the port blank. Press Set
Under rule 1 on the left, select Source > Group > Network Group, select 101-Subnet from the drop down. Press Set.
Press Commit.
Press Save.
10. Route your private VLAN with the private VLAN of the Vyatta Gateway Appliance in Gateway Appliances > Firewall Details Page
Login to the Softlayer console and Select Network from the drop down Menu > Gateway Appliances > Then click on the firewall.
Under the Associated VLANs > select our private VLAN (fakevlanid101) and click Actions > Route VLAN > update Device.
References
Network Gateway devices – Vyatta
http://knowledgelayer.softlayer.com/learning/network-gateway-devices-vyatta

