CREATE 802.1X WIRELESS NETWORK WITH SOPHOS UTM APs
Step-by-step guide
Prerequisites:
- UTM with Wireless Protection Subscription
- Sophos Access point
- Windows Server 2012 or newer
Windows Server required Roles & Features:
- Active Directory
- Active Directory Certificate Services
- Network Policy and Access Services
This article assumes the following:
- You have Active Directory installed and configured on your network
- You have the Network Policy and Access Services role installed
- You have a configured certificate authority or have a valid certificate you wish to use with NPS (Radius)
- Your AP is connected and functional on your UTM
1. Wireless Security Configuration
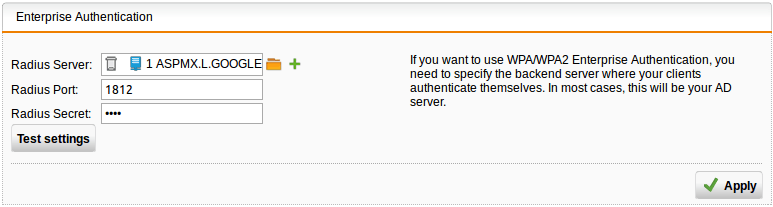
- Click on Wireless Protection > Global Settings > Advanced tab.
- Under the Advanced tab you must enter your Radius server, Radius port and your shared secret (this will be created by you)
2. Configuring RADIUS on your Windows Server
Authorise your Network Policy Server with your Active Directory
Radius Client Setup:
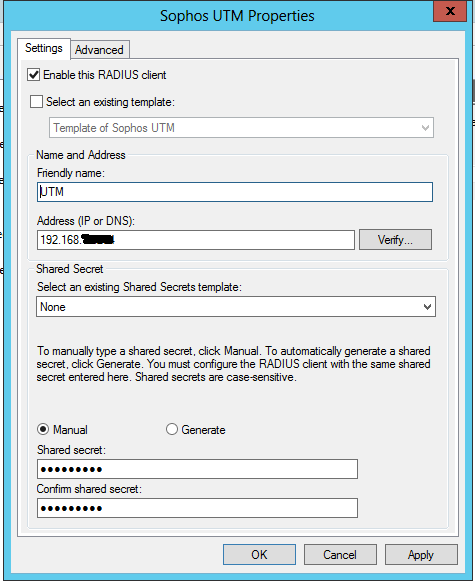
- Open Network Policy Server > Radius Clients and Servers > Radius Client
- Right click and select ‘New’
- Fill in like the image below with your Sophos UTM IP address and the shared secret you just created on the UTM and click Apply.
Policies
Connection Request Policies:
- Click on Policies
- Click ‘Connection Request Policies’.
- On the right, under Actions, click ‘New’.
- Enter a name, in our example we have called it “wireless”.
- Click Next.
- Now add the following conditions:
- Client Friendly Name: Name of the RADIUS client – in our case UTM
- NAS Port Type: Wireless – IEEE 802.11
- NAS Identifier: SSID of your wireless network – i.e. mywirelessnetworkname
- Click OK
- Click Next, then hit Finish – The default settings are fine for the rest of the configuration.
Network Policies:
Click Network Polices
- On the right hand side, click ‘New’.
- Name it, preferably the same as the Connection Request Policy
- Click Next
- Click Add
- Choose how you want to users to authenticate. For this, we are using the Domain ‘Users Groups’.
- Click Next until you arrive at Configure Authentication Methods
- We will use PEAP. Click Add and choose Microsoft: Protected EAP (PEAP)
- Choose the authentication method as shown above
- Click Next until you arrive at Configure Constraints
- Under NAS Port Type choose Wireless – IEEE 802.11
- Click Next, then Finish.
3. NPS Certificates:
Please make sure the certificate you are using has a valid subject as in the following screen shot – this can be found by Run > mmc > Add/Remove Snap-in > Certificates > Computer > Personal and then double click the RAS and IAS Server certificate you created earlier.
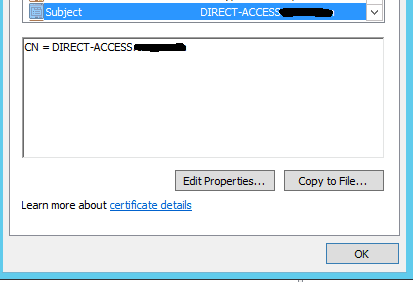
You can use your current certificate but we recommend creating a separate RAS and IAS certificate template if your Radius server is on the same machine as your Domain Controller. If you renew your Domain Controller cert it can stop authentication via Radius
The following links point to a few Microsoft KB articles describing how to deploy a CA and NPS Server Cert. You must follow the below links in order. Remember, this document outlines a fresh configuration. Please tailor this section according to how you have your certificates setup.

